
Methods and tools for opening locks
Content
- General. For all lock types
- Hammering of the locking bars
- Lever locks
- Twisting (screwdriver)
- Break-in of the deadbolt shank post
- Visual reading of the key code
- Trace method (impression)
- Self-setting (self-impression)
- “Kitbor” lockpick
- Set key
- Manipulation with two picks
- Manipulation with the combined picklock
- Key picking
- Cylinder locks. Cylinder security mechanisms.
- Bumping
- Pick gun
- Cylinder body-breaking
- Pulling the core
- Drilling of the case
- Core milling
- Manipulation
- Trace method (impression)
- Self-impression pins
- Visual method
- Reproduction of a copy
- Key selection
- Screwdriver
- Chemical hacking
- Removing the pins
- Cylinder knock-out
- Drilling around the cylinder
- Vandalism
1. General. For all lock types
1.1 Hammering of the locking bars

The method of breaking the lock is implemented with a percussion tool (hammer, sledgehammer), which, when accessing the ends of the bolts, the deadbolt is hammered into the lock case, followed by a breakage of nodes and details of the internal mechanism. The method is applicable to locks with any type of mechanism.
The main method of protection against this type of breaking is a protective pocket of the door frame, in which the bolts of the lock are inserted and which prevents the possibility of access to them. Additional measures are a specific hook shaped bolt (e.g. Abloy locks) as well as a special design of the lock case ensuring jamming of the deadbolt while it is being driven in.
2. Lever locks
2.1 Twisting (screwdriver)
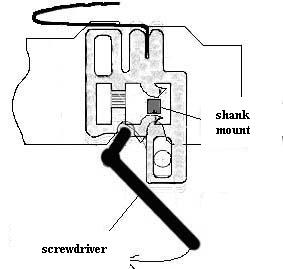
The purpose of the method is to break the shank of the deadbolt (the part by means of which the deadbolt is locked) or the code protrusions of the suvals and to push the deadbolt (the assembly of the lock which, when extended from the product body, locks the door leaf) into the lock case. The tool used during the process is similar to the one-beard key with the larger diameter rod and enlarged bit and is called the “screwdriver”. To protect against the screwdriver is usually a deliberate reduction of the strength of the teeth of the toothed rack of the deadbolt (the part of the shank plate of the deadbolt, on which are cut teeth for the rack gearing between the driving tooth of the key and the deadbolt).
When trying to open the lock, the screwdriver breaks the loosened teeth, but the shank of the deadbolt remains unharmed and further movement of the deadbolt becomes impossible.
Measures that make it difficult to use this method:
- protective plate (armor plate (steel plate with increased mechanical strength, installed between the lock and the outer sheet of the door leaf to protect against burglary methods such as drilling individual lock components)) or lock cover made of special metal with a hardened surface, installed in standard by the lock manufacturer;
- guard plate (armor plate) of special hardened metal to be installed in front of the lock in the door leaf;
- security lining (code, magnetic) that completely covers the keyhole in the door leaf.
2.2 Break-in of the deadbolt shank post


The method is based on drilling out the post of the shank of the deadbolt. There are two ways of breaking the post: the first is to drill out the post itself, the second is to drill out the plate (shank of the deadbolt) in the place where the post is fastened. The stand of the deadbolt shank is the main part for locking (stopping and fixing the mechanism parts in a certain position during their movements) of the deadbolt in most of the lever locks, when it is removed the deadbolt moves into the lock without any obstacles.
Measures that make it difficult to use this method:
- protective plate (armor plate) or lock cover made of special metal with a hardened surface, installed by the manufacturer of the lock;
- protective plate (armor plate) of special metal with a hardened surface, installed in front of the lock in the door leaf;
- direct protection of the post from drilling (hardened ball pressed (method of immovable connection of two parts without changing their forms due to plus difference in their dimensions) into the end face of the post or entire post made of heat-treated steel).
2.3 Visual reading of the key code
The method is based on the perpetrator’s ability to visually remember or photograph, unnoticed by the owner, his key. Then, using the obtained data, a duplicate key is made. This method is possible because of the peculiarity of construction of the majority of lever locks – a constant and known key secret slicing step.
Precautions:
- keeping keys out of reach of unauthorized persons, use of key locks;
- the use of locks with a complex key profile, difficult for visual recognition;
- the use of locks for which key blanks are available only to authorized dealers.
2.4 Trace method (impression)
This method consists in the fact that a specially prepared blank key is turned to open the lock with some force, then it is extracted and the characteristic contact points (traces) of contact of the key bead and plungers are determined. Then the height of the key secret is ground on those points. The process is repeated until a working copy of the factory key is made. The method requires a certain skill, good eyesight and a lot of time.
Measures that make it difficult to use this method:
- security lining (code, magnetic) that completely covers the keyhole in the door leaf;
- a cut-off barrier (bushing) built into the lock, partially or completely covering the keyhole of the door leaf;
- additional lock (latch) securing the door leaf vertical locking rods;
- stiffening springs of the suvolds.
2.5 Self-setting (self-impression)
This method is very similar to the previous one. The difference is that a special design tool with moving elements is used. When the tool is used, its moving elements are gradually displaced, up to a full match with the key code. The process of opening the lock is accelerated many times over in comparison to the trace method (impression). The danger of the method is that the attacker can easily close the lock after his “work” and use the picklocks for this type of locks more than once.
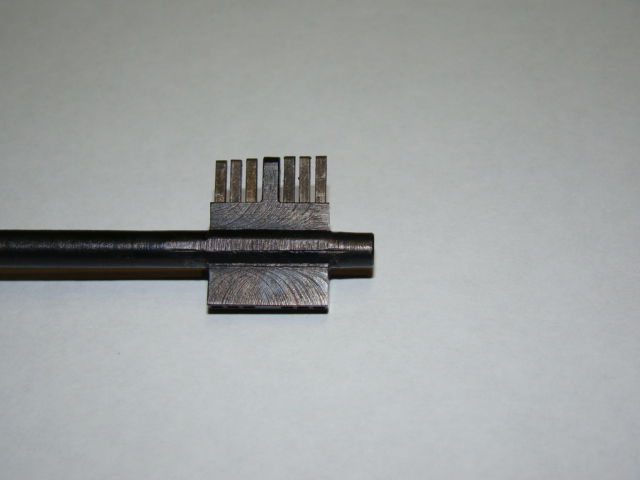
Measures that make it difficult to use this method:
- protective plates (code, magnetic), completely closing the keyhole in the door leaf;
- key recognition system;
- locking barrier (bushing) built into the lock, limiting or completely blocking the keyhole;
- additional lock (blocker) fixing the pull rods of the vertical lock of the attacked lock;
- stiffening springs of the suvalves;
- complex shape of the lock well.
2.6 “Kitbor” lockpick
The lock picking tool is adapted and named after technology developed in the USA. The pick to advance the deadbolt is placed in the corner of the bore and weights are attached to it during the tampering process. The second pick is placed in the bore of the lock to move the suvalds. There is no information on the use of this tool by the criminal, since it involves the use of more tools, unlike picks, which are easy to remove from the lock in case of danger.
Measures that make it difficult to use this method:
- cut-off bar (sleeve), built into the lock, partially or completely blocking the lock well;
- absence of “fifth tooth” on the shank rail, because in this case it is impossible to apply “kitbor” on the last, fourth movement cycle of the deadbolt;
- the system of false slots “key latch – shank column”;
- key recognition system,
- protection lining (code, magnetic), completely closing the keyhole in the door leaf.
2.7 Set key

Represents an imitation of a key. Consists of the base of the key and replacement elements – pins. A set of replacement elements contains all the heights of the key secrets for a particular lock or group of locks. The method is based on the gradual replacement of the pins. Two tools are involved, the set key itself and a master key for probing the pins. Gradual replacement of the pins is achieved by producing an exact copy of the key.
Measures that make it difficult to use this method:
- protective lining (magnetic, code), completely closing the keyhole in the door leaf;
- key recognition system;
- shutter (sleeve) that fully or partially covers the keyhole of the door leaf;
- key recognition system;
- lock release system with movable tumblers (CISA antipicking, Abloy SL 900).
2.8 Manipulation with two picks
This tampering method uses picks of a certain shape to both advance the deadbolt and raise the sway bars. There are different ways of inserting the picks within the bore of the lock. One pick is forced on the shank of the deadbolt and the other is used to gauge and move the pins. The process is repeated until the lock is fully opened.
Measures that make it difficult to use this method:
- the system of false slots “sleeve-shank column”, and their correct combination with the necessary spring stiffness;
- accuracy of manufacture of the pins;
- the code protrusions of the bit are rectangular in shape;
- pins with limited space for picklocks;
- key recognition system;
- key-recognition system with moving squeeze-bolts (CISA antipicking, Abloy SL 900);
- security plate (magnetic, code), completely closing the keyhole in the door leaf.
2.9 Manipulation with the combined picklock

The main difference of this lock pick is that its elements for moving the deadbolt and raising the suvald are located on the same longitudinal axis. The tool is installed in the center of the well, as well as the key of the lock, so for many locks this pick is a formidable weapon. There are different modifications of this tool, with its bearing on the edges of the chinks of the lock or on the key’s guide axis inside the lock.
Measures that make it difficult to use this method:
- the system of false slots “sleeve-shank column”, and their correct combination with the necessary spring stiffness;
- accuracy of manufacture of the pins;
- the code protrusions of the bit are rectangular in shape;
- pins with limited space for picklocks;
- key recognition system;
- key-recognition system with moving squeeze-bolts (CISA antipicking, Abloy SL 900);
- security escutcheon (magnetic, code), completely closing the keyhole in the door leaf.
2.10 Key picking
The method of opening the lock is based on an intruder trying to find the key to the sward mechanism. Low-quality locks have an increased gap between the shank post and the code protrusions of the sward. Because of this, the same lock can be opened with different-looking keys. This disadvantage is used by the criminal. The same method is applicable to locks with low secrecy, i.e. with a very small number of possible combinations of key secrets.
Measures that make it difficult to use this method:
- install locks that are not widely used;
- install locks with a secrecy of at least 25,000 key combinations;
- install locks according to the technical recommendations of the specialists;
- protective lining (magnetic, code), completely closing the keyhole in the door leaf.
3. Cylinder locks. Cylinder security mechanisms.
3.1 Bumping
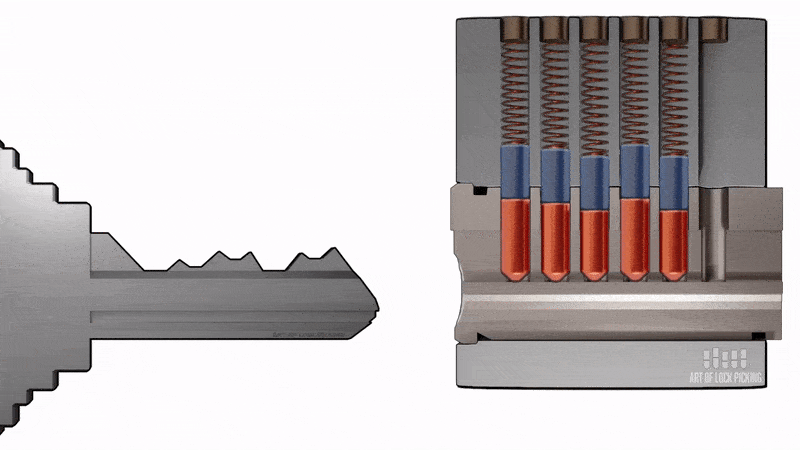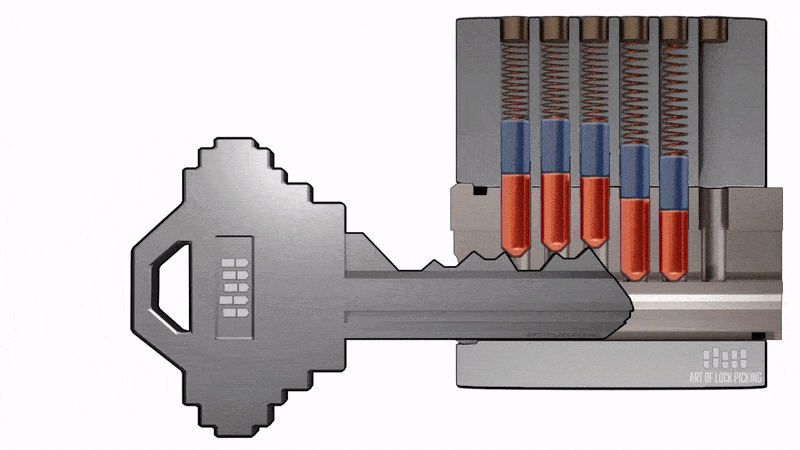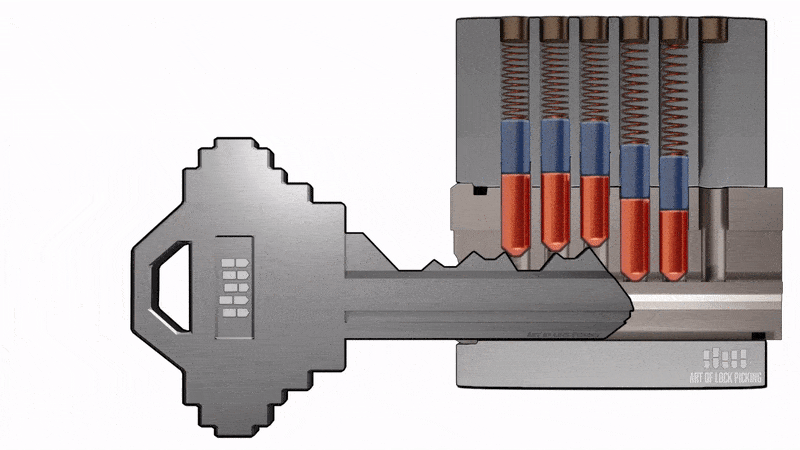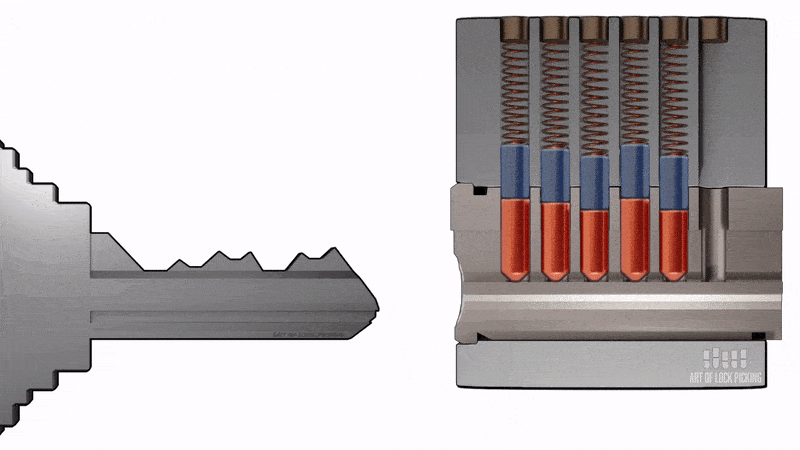
This method is dangerous only for cylinders with a secrecy pin mechanism (a mechanism consisting of code pins and locking pins securing the core. The height of the code pins corresponds to the secrets of the key. When the key is inserted the pins come out on the slot line and the key rotates the core to move the deadbolt). It is based on a simultaneous impact on all the pins of the secret mechanism with the simultaneous application of force to the core (movable part of the secret mechanism of cylindrical shape, driven by the key, which has a guiding (profile) slot to install the key, channels for placing the pins (frames), the assembly of torque transfer to turn the cam, protective elements) of the cylinder mechanism in the direction of opening the lock. A specially prepared blank key is used for tampering. The presence of protective pads with a slot for the key does not save the use of this method.
There are a number of design solutions to protect against bumping:
- other (not pins) principle of the device (e.g. EVVA 3KS, Abloy, frame cylinders);
- combined cylinder locking mechanisms with different types of locking elements (frames + pins);
- additional recognition elements in the secret mechanism and the key (the so-called interactive elements);
- Cylinder locking mechanisms with disc secrecy elements (Abloy);
- the use of protective pads that completely closes access to the end of the locking mechanism (magnetic, code) pads.
3.2 Pick gun

A special tool for simultaneous striking of the locking mechanism cylinder pins. While striking the pins, an attempt is made to rotate the core. Two tools are involved, unlike bumping. There are both mechanical and electromechanical designs (electro-peak). The presence of protective pads with a slot for the key does not save this method.
Measures that make it difficult to use this method:
- other (not pins) principle of the device (e.g. EVVA 3KS, Abloy, frame cylinders);
- combined cylinder locking mechanisms with different types of locking elements (frames + pins);
- additional recognition elements in the secret mechanism and the key (the so-called interactive elements);
- Cylinder locking mechanisms with disc secrecy elements (Abloy);
- the use of protective pads that completely closes access to the end of the locking mechanism (magnetic, code) pads.
3.3 Cylinder body-breaking

The method is based on the attempt of the perpetrator to break the cylinder body into two halves. The breaking of the case occurs by the hole of the screw that fastens the cylinder. Methods and tools for this type of burglary have been developed quite a lot. Grabbing the case to break it occurs both through the key hole of the core and directly by the case itself, protruding beyond the plane of the door leaf.
Measures that make it difficult to use this method:
- the use of protective plates (armour plate, magnetic plate, code plate), and if they cannot be used, at least take measures to prevent the dismantling of the fittings;
- when making the door, the cylinder mechanism must not protrude more than 3 mm beyond the surface of the door leaf;
- Exact dimensions of the cylinder hole in the door leaf;
- restricting access for gripping the cylinder body with additional elements;
- use of cylinders with case-breaking protection (steel inserts or, on the contrary, deliberate loosening of the case).
3.4 Pulling the core
The method is based on the fact that the offender uses a special tool to try to pull the core out of the cylinder housing. The code and locking pins in this operation are simply cut along the connector line. The core is grabbed by the edges of the key channel in order to pull it out.
Measures that make it difficult to use this method:
- the use of protective covers that completely block access to the end of the cylinder mechanism (magnetic, code).
3.5 Drilling of the case

In this method of burglary, the culprit drills out a channel in the end of the cylinder housing, through which the remains of the pins and their springs are subsequently removed. The core is then simply turned with a screwdriver.
Measures that make it difficult to use this method:
- use of protective covers (armor plate, magnetic cover, code cover);
- use of cylinders with heat-treated metal protective inserts in their design, preventing drilling of the working elements of the cylinder mechanism.
3.6 Core milling
The breaking-in takes place with a special boron cutter. The body of the core of the cylinder mechanism or part of it in the area of the code pins is milled. Then the rest of the core is turned in the opening direction. The presence of protective elements does not save this method, as the boron cutter is highly resistant.
Measures that make it difficult to use this method:
- manufacturing of the housing from steel;
- use of security plates (armor plates);
- the use of protective plates, completely closing the access to the end of the cylinder mechanism (magnetic, code).
3.7 Manipulation
This method of tampering uses lock picks of a certain shape. One tool is applied to turn the core, the other is used to probe and move the pins. The process is carried out before the core is turned and therefore the lock is opened.
Measures that make it difficult to use this method:
- high precision of manufacture of the cylinder mechanism elements;
- complex profile of the key channel, which creates inconveniences for manipulation;
- use of cylinders with pins of a certain shape in the construction of the mechanism, making it difficult to open the cylinder mechanism (“mushroom” or “coil” shape of the pins);
- use of a cylinder mechanism with several independent rows of pins;
- use of combined cylinder mechanisms with different types of secret mechanism elements (frames + pins);
- use of cylinder mechanisms with “telescopic” pins;
- use of protective pads, completely closing the access to the end of the cylinder mechanisms (magnetic, code pads).
3.8 Trace method (impression)
This method consists in turning the blank key in the core of the cylinder mechanism in the direction of opening the lock with a certain force according to a certain technique. After that, the blank is removed and the characteristic contact points (traces) of the contact between the working edge of the key and the code pin are determined. Then the height of the key secret is lowered in those points. The process is repeated until an exact copy of the key is made. The process is much faster compared to the plunger lock.
Measures that make it difficult to use this method:
- use of protective covers that completely close access to the end of cylinder mechanisms (magnetic, code);
- use of cylinder mechanisms with horizontal location of the keyhole (key with vertical milling);
- use of combined cylinder mechanisms with different types of secret mechanism elements (frames + pins);
- use of cylinder mechanisms with “telescopic” pins.
3.9 Self-impression pins
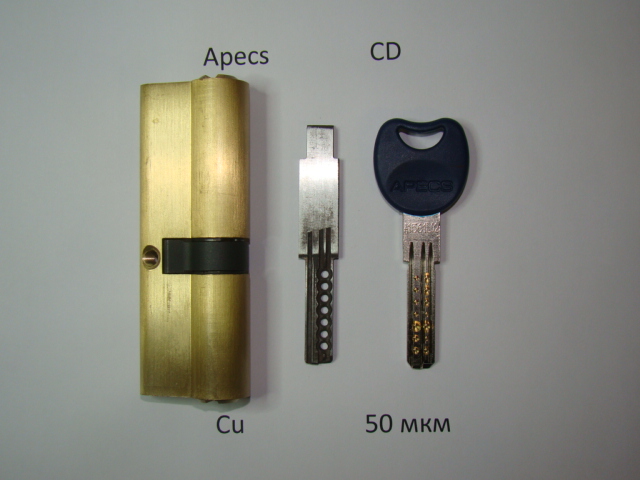
A specially prepared key blank, which has a plastic working surface capable of being deformed, is inserted into the lock core. According to a certain technology, in the course of the opening, the pins are self-installed according to the key code and the core is turned in any direction. The danger of the method is that the criminal can easily close the lock after his “work” and use the picklock more than once. Compared with the trace method (impression), the process is much faster.
Measures that make it difficult to use this method:
- the use of protective plates, completely blocking the access to the end of the Cylinder mechanism (magnetic, code);
- use of combined cylinder mechanisms with different types of secret mechanism elements (frames + pins);
- use of a cylinder mechanism with “telescopic” pins;
- use of a cylinder mechanism with a complex shape of the key channel profile.
3.10 Visual method
The method is based on the fact that the criminal knows the pitch of the key’s secret height slices for a particular cylinder mechanism. This makes it possible, having certain skills, to visually determine and remember the code of the key, or secretly photograph the key. Then a duplicate key is made.
Measures that make it difficult to use this method:
- storage of keys in a place inaccessible to prying eyes, the use of key boxes;
- use of a cylinder mechanism with combined secrecy elements and other additional details that make it difficult to visually read the key code;
- use of the cylinder mechanism, key blanks for which are available only to authorized dealers.
3.11 Reproduction of a copy
This technique is used by criminals if they get their hands on your key for a short time. You can take a picture of the key, make an impression or make a duplicate at the nearest key shop.
Measures that make it difficult to use this method:
- the use of a cylinder mechanism for which key blanks cannot be made without specialized tools and equipment;
- the use of a cylinder mechanism for which key blanks are only available from authorized dealers.
3.12 Key selection

The method of opening the lock is based on attempts by an intruder to find the key to the cylinder mechanism. Low-quality locks have a shape of pins, compensating for the low precision of production (rounded, as opposed to high-quality cylinders). As a result, the same lock can be opened with keys of different cuts. This disadvantage is used by the criminal. The same method may be used with locks of low secrecy, i.e., with a very small number of possible combinations of key secrets. Cylinder mechanisms, which are very popular in the region, are exposed to a greater risk.
Measures that make it difficult to use this method:
- refuse to install a low-quality cylinder (the distinctive feature is the low cost of the cylinder);
- to install less popular cylinder mechanisms that are not very popular;
- use of protective covers that completely close access to the end of the cylinder mechanism (magnetic, code).
3.13 Screwdriver

The method is based on an attempt to forcibly rotate the core of the cylinder mechanism. To perform this operation, a solid steel billet is made to the shape of the profile of the key channel of the core. During the burglary, the secrecy elements of the cylinder mechanism are destroyed and the core is rotated.
Measures that make it difficult to use this method:
- the use of protective covers that completely close access to the end of the cylinder mechanism (magnetic, code);
- refusal to install a low-quality cylinder (their price is a distinctive feature);
- use of cylinders with stronger steel pins in their design;
- use of a cylinder mechanism with a complex profile of the key channel.
3.14 Chemical hacking
Cylinder mechanisms with a single row of pins located along the vertical axis and at the bottom of the cylinder are more susceptible to the method. A chemical reagent (concentrated acid) is poured into the body of the cylinder mechanism, which dissolves the springs under the pins. Once the springs have dissolved, the pins are lowered into the channels and the core can be turned with a screwdriver.
Measures that make it difficult to use this method:
- use of protective overlays that completely close access to the end of the cylinder mechanism (magnetic, code);
- use of cylinders, in which the total length of the housing pin and the core pin will exceed the length of the code channel to the socket line;
- use of cylinder mechanisms having pins in the upper part of the housing;
- use of combined cylinder mechanisms with different types of secret mechanism elements (frames + pins).
3.15 Removing the pins
A plastic mass is deliberately pushed into the core, through the key channel, which, after filling the inner space, begins to push the code pins beyond the connector line between the core and the cylinder housing. The core is then turned with a screwdriver in the direction of the lock opening.
Measures that make it difficult to use this method:
- use of protective overlays that completely close access to the end of the cylinder mechanism (magnetic, code);
- use of cylinders in which the total length of the housing pin and the core pin will exceed the length of the code channel to the socket line;
- use of cylinder mechanisms that do not have a closed space of the core key channel;
- use of combined cylinder mechanisms with different types of secret mechanism elements (frames+pins) or balanced (Abloy, Evva 3KS, etc.).
3.16 Cylinder knock-out
The perpetrator hits the cylinder housing hard in order to dislodge it inside the room. The cylinder fixing screw, in such an attempt to break in, is simply sheared off by a heavy load. After removing the cylinder, it is possible to advance the deadbolt to open the lock. Do not install cylinders that have a driving cam flush with its body. The cam should protrude a little, so it creates an additional obstacle when beating out, resting against the lock body.
Measures that make it difficult to use this method:
- the use of protective plates that completely close access to the end of the cylinder mechanism (magnetic, code);
- the use of security plates with a slot for the key (armor plate);
- use of the cylinder mechanism with a turning of the drive cam.
3.17 Drilling around the cylinder
Knowing the mechanism of the lock, the culprit drills into the door leaf and the lock case at the desired point. Then he lifts the lock pin and advances the deadbolt towards the opening direction.
Measures that make it difficult to use this method:
- when ordering the door, pay attention to the presence of a protective armor plate that covers the danger zone;
- the use of protective plates mounted on the outside of the door leaf, covering the danger zone (magnetic, code plates);
- If a standard armor plate is available, specify whether it protects against drilling around the cylinder.
3.18 Vandalism
Using the vulnerable point of the cylinder mechanism – the open key channel, the offender uses improvised means to disable the cylinder mechanism (by hammering with matches, pouring glue, etc.). The meaning of this in the calculation that the owner of the apartment can not immediately replace the cylinder with a similar, temporarily replacing it with a simple one. After replacing the damaged cylinder mechanism for a cheaper one, there is an attempt to break in while the “native” cylinder mechanism is being repaired. If there is no cylinder mechanism at hand (there was no replacement), the door becomes less burglar-proof while the cylinder is being repaired, which is what the criminals are trying to do.
Measures that make it difficult to use this method:
- the use of protective covers that completely close access to the end of the cylinder mechanism (magnetic, code);
- Provide for a second, spare cylinder at home.
This article describes the most commonly used methods of opening door locks. These methods are used by both intruders and special emergency services. Our tool is intended only for professional use in the work of locksmiths as well as first responders.
best lockpicking tools, collection of Lock Picks, lock pick, lockpicking tools, locksmith, Locksmith gadgets for doors, Tools professional